A Strategic Approach to Addressing Security Breaches
Firstly, organizations must prioritize preventive measures to fortify their defenses against potential threats. This includes implementing robust access controls, encryption protocols, and network segmentation to safeguard critical assets and sensitive data. By proactively identifying and addressing vulnerabilities in their systems, organizations can significantly reduce the likelihood of security breaches occurring in the first place.
Establishing a culture of security awareness and training among employees is paramount. Educating staff about cybersecurity best practices, phishing awareness, and incident response protocols can empower them to detect and mitigate potential threats effectively. Additionally, regular security audits and assessments can help identify weaknesses and gaps in existing security measures, allowing organizations to take corrective action promptly.
Furthermore, investing in advanced technologies such as artificial intelligence (AI), machine learning (ML), and behavioral analytics can enhance threat detection and response capabilities. These technologies can analyze vast amounts of data in real-time, enabling organizations to identify abnormal behavior and potential security breaches more accurately and efficiently.
In addition to preventive measures, organizations must also focus on building a resilient infrastructure capable of minimizing the impact of security breaches when they occur. This involves implementing robust incident response plans, establishing clear communication channels, and implementing effective recovery strategies. Organizations can mitigate the damage caused by breaches and restore normal operations swiftly by having a well-defined incident response framework in place.
Moreover, leveraging threat intelligence and information-sharing initiatives can enhance situational awareness and enable organizations to stay ahead of emerging threats. Collaborating with industry peers, government agencies, and cybersecurity experts can provide valuable insights into evolving threat landscapes and help organizations better prepare for potential security breaches.
Use Case
I keep up my blogs purely as a pastime. This project is not multibillion-dollar. It's just a simple stupid project with no nonsense. I merely would like to talk about the professional experiences I've had. I was dealing with serious cyberattacks on my ecosystem not too long ago. Without God's assistance and resilience, I could never continue to endure in this abrupt era.
In my humble view, in the event of a serious security compromise, there are a few major measures that one person should take to restart the ecosystem.
- First things first, always maintaining attitudes of "stay calm, do not panic, do not rush, and seek refuge in The Almighty".
- Executing backups as frequently as feasible.
- Revamping the security paradigm regularly, and implementing the updated security protocols within the ecosystem concurrently.
- Setting up its security settings to the maximum possible level and executing workflows to apply an online wizard to restore the dead client operating system(s) in the event of OWASP attacks, remote code execution, and zero-day threats.
- Reinstalling the server(s) and recovering the repositories swiftly in the event of a serious cyberattack.
- Staying vigilant regarding impending security risks.
- Minimizing the number of mitigation operations if a series of security breaches reoccur by continuously and adaptively learning the patterns of cyberattacks.
- Collecting information about emerging discovered security flaws regularly.
Thankfully, the web and mobile apps are now ready to run in return, and enclosed are the screenshots representing the real-time multiple-face recognition apps, both web and mobile versions as follows.
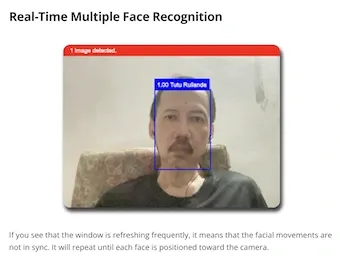
It's the web app version
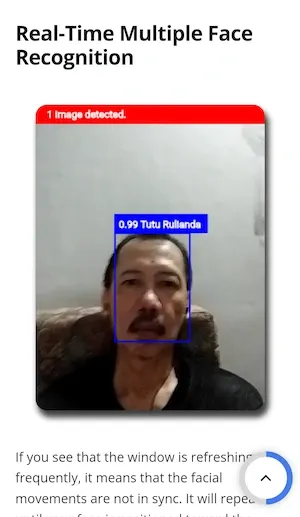
It's the mobile app version
Conclusion
While mitigation efforts remain essential for addressing security breaches, adopting a proactive approach focused on minimizing vulnerability and exposure is paramount. By prioritizing preventive measures, investing in advanced technologies, and building a resilient infrastructure, organizations can significantly reduce the likelihood and impact of security breaches. Embracing this strategic approach will not only enhance cybersecurity posture but also instill confidence and trust among stakeholders in an increasingly interconnected world.
Updated: February 18, 2024 - 11:46AM (UTC+7)